“I can tell you that in the digital world, we don’t really have privacy,” said Gary Liu, founder of the cybersecurity startup Terminal 3, as he sat down for an interview. “It sounds scary, but that’s the reality.”
This isn’t alarmist rhetoric; it’s an insight drawn from Liu’s firsthand experience at the forefront of Silicon Valley’s tech industry. A veteran of the technology and media worlds, Liu knows exactly how data is stored, transmitted, and exchanged. He has led product experiments at Spotify, served as CEO of the once-popular social platform Digg, and held roles at Google and AOL.
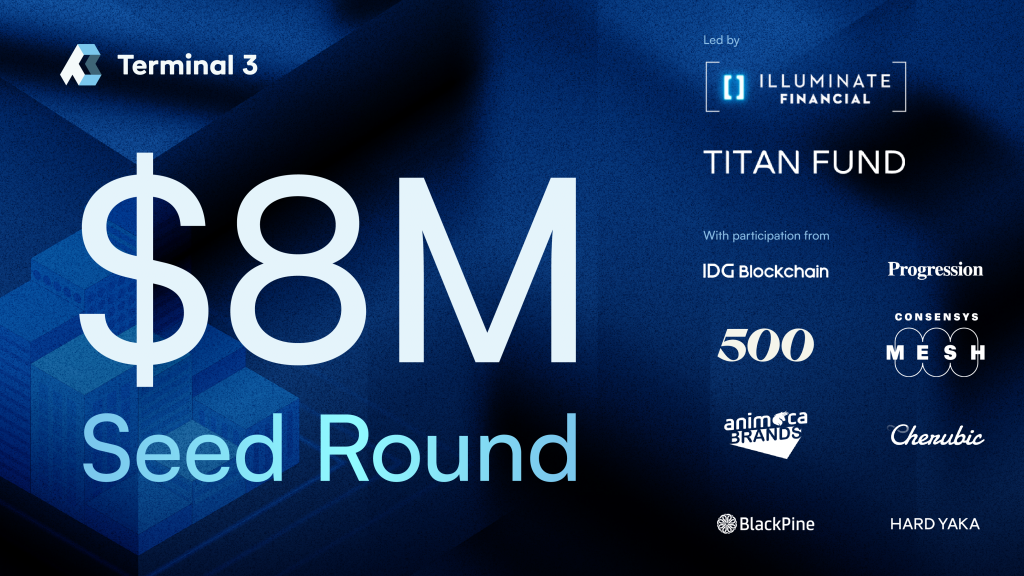
In 2016, Liu made a dramatic shift to become CEO of the South China Morning Post, where he spearheaded the century-old newspaper’s digital transformation. These experiences revealed a troubling truth: while users generate massive amounts of data, they have almost no control over where it goes or how it’s used.That realization sparked the idea for Terminal 3. In just one year, this Hong Kong–based startup has enabled more than 10 million users to store and manage their personal data through its enterprise services. It recently completed an $8 million seed funding round backed by several world-class investment firms.
What exactly does Terminal 3 do?
At the core of Terminal 3’s architecture lies a platform called “Oracle.” But this Oracle isn’t the same as the blockchain oracle used to bridge on-chain and off-chain data. Instead, it’s a decentralized data hub where users retain ownership of their data while still being able to provide trusted authentication to businesses when needed.
Liu explained that Oracle’s key functions include helping users securely store data in a decentralized manner, enabling encrypted computation and processing through privacy-enhancing technologies (PETs), and giving users control over how applications query and use their data—all without ever exposing the original information. This allows organizations to verify identities, ensure compliance, and even conduct advanced data analysis without accessing personal data.
Terminal 3’s foundation is built on blockchain, while its data processing core relies on PETs such as Zero-Knowledge Proofs (ZKP), Multi-Party Computation (MPC), and Trusted Execution Environments (TEE). These technologies enable enterprises using Terminal 3 to perform identity verification and compliance checks without ever holding users’ data themselves. This approach not only greatly reduces the risk of data breaches and compliance costs, but also makes data access more secure and efficient.
Sounds complicated? “What we’re doing is enabling businesses to legally and securely verify information without actually owning the data,” Liu explained. “For example, a bar only needs to know if you’re over 21; it doesn’t need your full birthdate. That used to be very difficult, but with Terminal 3, organizations can now achieve it through zero-knowledge verification—ensuring both compliance and privacy protection.”
“Or consider banks,” he continued. “If they want to verify whether someone is a qualified investor, they typically have to request account details and proof of assets—an approach that’s cumbersome, time-consuming, and labor-intensive.
But with Terminal 3, financial institutions can receive a verified certificate that simply confirms ‘this person is eligible,’ without ever accessing sensitive data.” This, he added, has major applications in the financial sector for KYC and anti–money laundering (AML) compliance.
Finally, Liu described a potential cross-border use case: “When you travel abroad, you carry your passport not just for the airport, but also for hotel check-ins, tax refunds, and even boarding trains. Now we can convert passport information into an anonymous, verifiable certificate, store it securely on your phone, and present it via a QR code to prove your identity—without handing over a stack of personal data. These are the kinds of solutions companies can achieve by adopting Terminal 3.”

The Rise of Data Sovereignty
This shift toward data sovereignty didn’t happen overnight. In recent years, decentralized technologies have steadily moved into the mainstream, and more businesses and governments are beginning to see blockchain as a critical piece of modern infrastructure. People are increasingly recognizing that data shouldn’t be centrally controlled; it should be owned and authorized by individuals themselves.
Regulations have also emerged as a major driving force behind this trend. From the European Union to the United States and across many Asian countries, governments are tightening personal data and privacy protection policies. Companies are now required to implement clear authorization and traceability mechanisms across data collection, storage, and access. For businesses, this is no longer just an ethical choice—it’s a legal mandate.
Meanwhile, user expectations of digital experiences are shifting. In the past, a service was considered satisfactory if you could simply log in without issues. Today, people expect a cross-platform, seamlessly integrated identity system: Can an identity created on one platform be trusted on another? This demand is placing new pressures on the core infrastructure of enterprises.
Finally, perspectives on national security are evolving. More governments now recognize that data lies at the heart of digital sovereignty—and that controlling it is essential for safeguarding citizens’ information. Terminal 3 isn’t just an enterprise solution; it’s a direct response to the urgent global need for data control and trust.

A New Data Governance Infrastructure
To enable enterprises to handle authentication, authorization, and governance without directly accessing user data, Terminal 3 has divided its technical capabilities into three product lines—Identity, Verify, and Agent Auth—each designed for a specific data application scenario.
Identity is a decentralized identity system that helps organizations manage user accounts, registrations, single sign-on (SSO), and data permissions. It also features a built-in lightweight CRM for user segmentation and communication.
Unlike traditional IAM (Identity and Access Management) systems like Okta or Ping, which store data centrally on enterprise servers, Terminal 3 uses a decentralized framework in which user data is held by individuals and authorized through encrypted certificates. This approach allows enterprises to complete identity verification and compliance checks without accessing raw data, reducing both security and regulatory risks.
Additionally, Terminal 3 integrates zero-knowledge encryption with decentralized storage to offer enhanced security, seamless cross-platform interoperability, and high flexibility—positioning it not just as a replacement for conventional IAM systems, but as the foundation for next-generation identity governance.
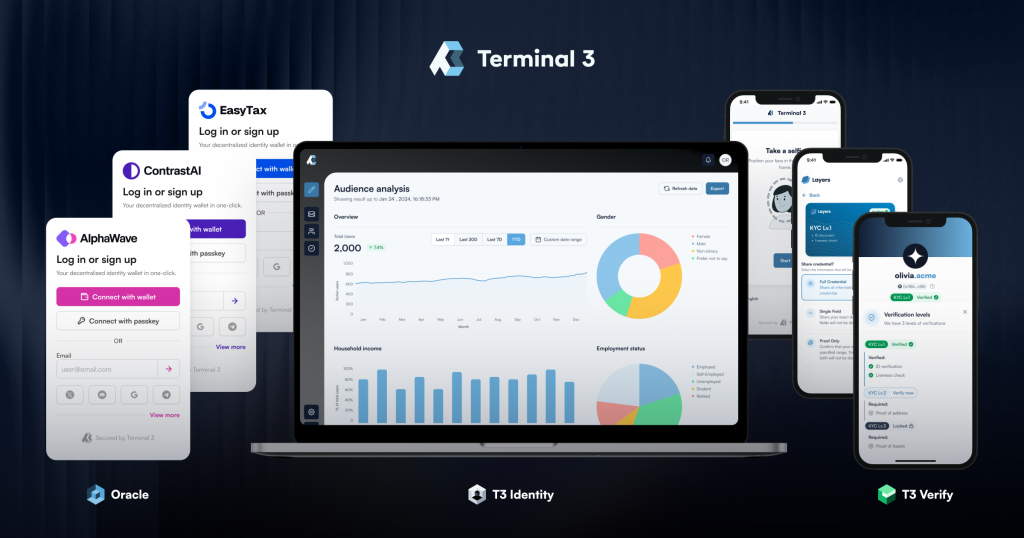
Verify expands the possibilities for identity applications. Enterprises can use this module to verify a variety of conditions—such as membership status, specific qualifications, or even ownership of digital assets—all through zero-knowledge verification. This is particularly attractive to government agencies and highly regulated industries like finance.
Agent Auth is Terminal 3’s solution for the AI era. As AI agents increasingly take on tasks traditionally handled by humans—like searching, shopping, and signing contracts—both businesses and users need new ways to confirm these actions are properly authorized.
“In the future, we won’t be physically present in every digital space, but identity and authorization will still need to be verified,” Liu explained. Agent Auth lets users explicitly authorize AI to access personal data and execute transactions on their behalf through secure mechanisms that transmit information, such as payment details, directly to the platform instead of leaving it to the AI. This ensures every action happens under controlled, traceable authorization.
$8M Seed Round Secured
Terminal 3’s three product lines are strategically aligned with distinct target audiences: T3 Identity serves Web3-native teams, T3 Verify targets governments and highly regulated sectors like finance, and Agent Auth supports AI ecosystems and platforms that require agent behavior verification. This clear market segmentation not only sharpens Terminal 3’s focus but also speeds alignment with real-world needs.
Yet realizing the vision of “verification without data” has proven far more challenging than it sounds. Liu admits the team had to build an almost unprecedented infrastructure entirely from scratch, spending 18 months refining the technology and educating the market to gradually earn trust. The journey was demanding, but as the product matured and enterprise users came on board, new opportunities began to emerge.
Since its launch just over a year ago, Terminal 3 has formed partnerships with multiple blockchain platforms, Web3 companies, and enterprises, collectively serving more than 10 million users. Backed by leading investors—including Illuminate Financial, CMCC Global (Titan Fund), Animoca Brands, IDG Blockchain, 500 Global, and Cherubic Ventures—the team has laid a solid foundation for future expansion.
Creating a Foundation of Trust for a New Era
“What’s not going to change in the next 10 years?” Amazon founder Jeff Bezos once reminded entrepreneurs that the best bets are on essential needs that stay constant, no matter how the world evolves.
For Liu, these “unchanging truths” are clear: data must be verified, identities must be validated, and compliance must be enforced. That’s precisely what Terminal 3 is building—a trustworthy foundation for data processing using the most rigorous technologies available.
When asked about his long-term vision, Liu expressed admiration for three largely unseen yet essential infrastructure companies: Stripe, Plaid, and Twilio. While consumers rarely think about them, these companies power nearly every online payment and video call.

“I want Terminal 3 to be like these companies—quietly upholding the foundation of trust in the data world,” he said. “Whenever an application needs to access user data—whether for age verification, KYC, or identity checks—we’re there behind the scenes to ensure privacy and legitimacy.” It may not be a name that consumers mention often, but it has the potential to become one of the most trusted infrastructures of our time.
This article has been contributed to Asia Tech Daily.